Block user access over weekend to your resources
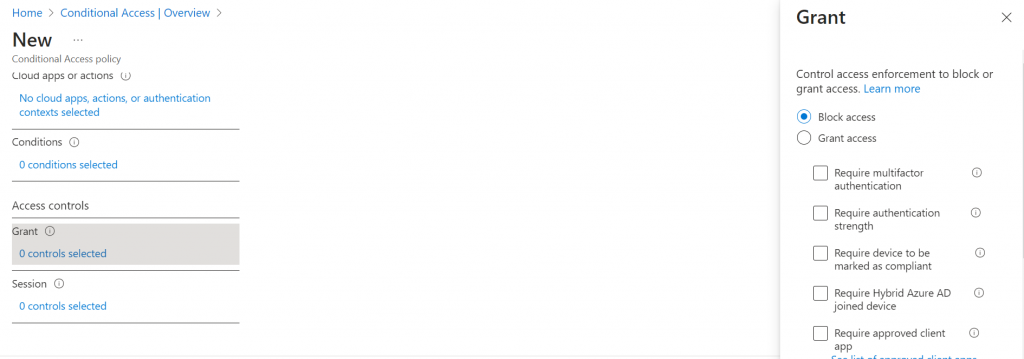
Using a Conditional Access Policy
Azure AD conditional access policies run after a user successfully authenticates to decide whether they can connect to the requested resource. Membership of a group is one of the supported conditions, meaning that it is easy to create a policy to block access to apps for a group. Because it’s weekend access we want to block, we could add another condition to say that access is OK if the user is in a corporate location, but not if they are at home or anywhere else.
Figure shows the outlines of such a policy. Anyone specified in the Blocked Weekend distribution list (you can also use a security group or Microsoft 365 group) is blocked if they attempt to access an Azure or Office 365 app:
When a user attempt to access an app is blocked by a conditional access policy, they are told that their sign in was successful (authentication worked), but they don’t have permission to access the resource.
If they are already connected to an app and the app attempts to renew its access token, the conditional access policy will block issuance of the token.
Controlling Conditional Access Policies with PowerShell
Conditional access policies allow organizations to exert granular control over the access users have to apps. In our scenario, we want to allow free access during the week. We could disable the conditional access policy during the working week and enable it just for the weekend. This is easily done by editing the policy in the Azure AD portal or with PowerShell.
For example, here’s how to enable the policy:
$PolicyId = Get-AzureADMSConditionalAccessPolicy | ? {$_.DisplayName -eq "Block Weekend Access"} | Select -ExpandProperty IdSet-AzureADMSConditionalAccessPolicy -PolicyId $PolicyId -State Enabled
To disable the policy after the weekend, run:
Set-AzureADMSConditionalAccessPolicy -PolicyId $PolicyId -State Disabled
You can create an Azure Automation account and Schedule the powershell scripts for your specific timings.
Make sure you apply the policy to a specific group and not locking out yourself from the tenant.


